Passwords, while convenient, are inherently flawed in how they can be abused. If someone gets your password, a single factor of authentication, they can often gain access to your online accounts. That's why we have the likes of two-factor authentication, which combines something that you know with something that you have, such as your smartphone. However, in the case of you using something like an SMS code, someone could, in theory, spoof your phone number and take that code. It's not totally secure and there are multiple potential entry points for a would-be attacker. That's why passkeys, which Google has announced it's bringing to both Android and Google Chrome, are important.
Earlier this year, Apple, Google, and Microsoft announced that they will be adopting the FIDO standard for passkeys on all major platforms by next year. This would make passwordless sign-ins more commonplace across the internet. How it works is simple -- on Android, it'll turn your smartphone into a passkey that can be used to log in to a website. These passkeys are then synced through the Google Password Manager for easy access across your devices and on your computer, too. While it will start with support for websites only, the idea is that developers will be able to implement it in their apps, and even support passkeys that may have already been used to log in to the same service in the user's browser.
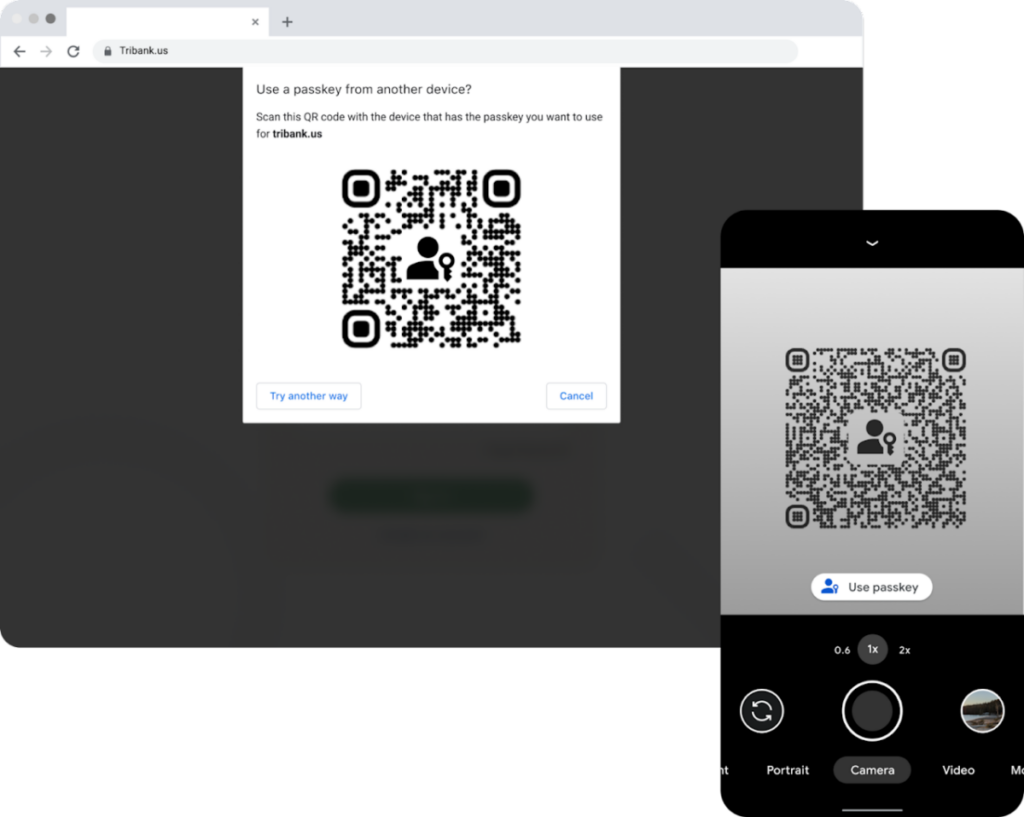
In case you're worried about ecosystem lock-in, Google has assured users that this won't be the case as they're built on industry standards. Passkeys are platform-agnostic, meaning that you can even log in to services that support passkeys using a Mac running Safari. You'll be presented with a QR code that you scan on your Android smartphone. The same will work vice versa with a passkey stored on an iPhone to log in to services in Google Chrome.
Passkeys make it so that without the key stored in your account or on your phone, somebody can't log in to any of your online accounts -- no matter how hard they try. There's no phone number to spoof, nothing to steal (unless they steal your phone and log in to that), and no password to crack. They simply won't be able to get in unless they are able to convince the service provider to give them access -- in which case, that was always a vulnerable entry point for whatever account you were using anyway.
If you want to try it out, developers can enroll in the Google Play Services beta and use Chrome Canary, as a stable rollout is expected later this year. The WebAuthn API can be implemented on websites for compatibility with passkeys in Google Chrome, Android, and other platforms. An API is also expected to be released later this year for native Android apps.
Source: Google